
Production Server Architecture | Scalable & Secure Infrastructure
Production Server Architecture | Scalable & Secure Infrastructure
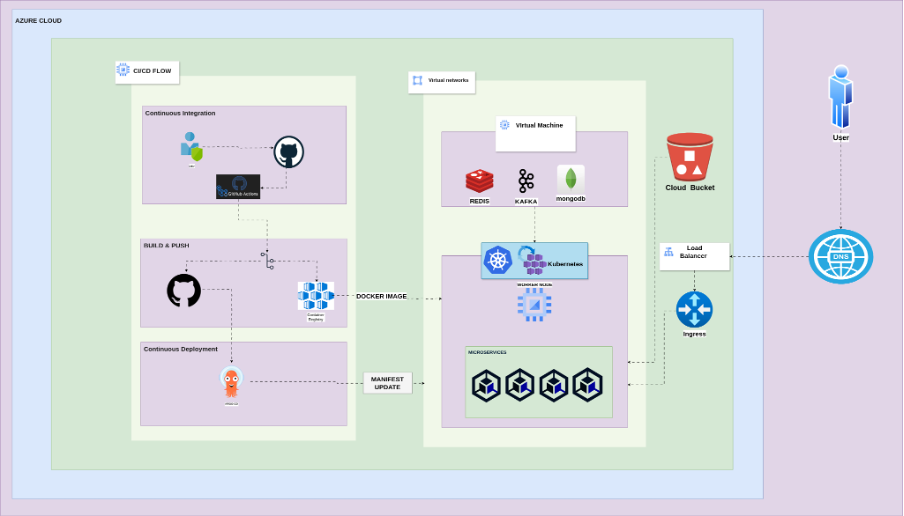
1. Project Overview
The Libertum Asset Tokenization project aims to create a robust system for tokenizing assets. The system architecture is designed to ensure scalability, high availability, and fault tolerance by leveraging various cloud and container technologies.
2. Infrastructure Setup
Azure Virtual Network (VNet):
To establish a secure, isolated Azure environment with segmented network traffic for different services, minimizing public exposure and ensuring secure on-premise connectivity.
VNet Design
Subnets:
● Public Subnet: Hosts resources needing internet access (e.g., web servers, load balancers). Connected to the Internet Gateway.
● Private Subnet: Hosts internal resources (e.g., databases, backend services) with private IPs. Outbound traffic is routed through a NAT Gateway for secure internet access.
Security Configuration
Network Security Groups (NSGs):
● Public Subnet NSG: Allows inbound HTTP/HTTPS traffic and outbound traffic to the internet.
● Private Subnet NSG: Restricts inbound traffic to internal services and allows outbound internet traffic via NAT Gateway.
● Private IP Communication: Services in the private subnet use private IPs to communicate internally, with no direct exposure to the internet.
NAT Gateway Configuration
● Outbound Internet Access:
NAT Gateway provides private subnet resources with outbound internet access via a static public IP, ensuring no inbound public traffic.
Security Measures
● Network Isolation: Subnets and NSGs ensure controlled traffic flow.
● Firewall & Monitoring: Optional Azure Firewall for additional protection and Azure Monitor for traffic logging and auditing.
Virtual Machine
Backend Services Server
● Instance Name: prod-Kafka-redis-libertum
● Machine Type: Azure Virtual Machine (VM) with Ubuntu 22.04
● Specs: 2 vCPUs, 4 GB memory,
● Boot Disk: 30 GB
● Networking: Configure appropriate network settings
● Firewall: Allow necessary traffic for your services
Additional Services:
Kafka:
Description: The Kafka server facilitates real-time data processing and streaming, supporting use cases like event-driven architectures, log aggregation, and message queuing. It ensures seamless communication between different components of the system.
Redis:
Description: Redis is used for caching, enhancing application performance by storing frequently accessed data in memory, thus reducing latency. It significantly improves the response time for user-facing applications.
MongoDB:
Description: MongoDB will be set up as a service on the Virtual machines, serving as the primary database for storing structured and unstructured data used by various services.
Kubernetes Cluster (AKS)
● Description: The Kubernetes cluster will be deployed on Azure Kubernetes Service (AKS) for scalable container management. AKS ensures high availability, automated updates, and robust security. The cluster will span multiple availability zones for fault tolerance, with auto-scaling to adjust nodes based on demand
Cluster Specifications:
Node Size: 2 cores, 8 GB RAM
Workloads:
● Deployments, StatefulSets, and DaemonSets for managing workloads.
● Services and Ingress controllers for traffic routing.
Backend Services on Azure Kubernetes Service (AKS):
Objective:
To deploy backend services, including microservices and APIs, on Azure Kubernetes Service (AKS), leveraging AKS features such as automatic scaling, self-healing, and seamless integration with Azure Cloud services. The setup ensures high availability and efficient management of diverse workloads.
Horizontal Pod Autoscaler:
Automatically adjusts the number of pods in a Kubernetes deployment based on observed metrics, such as CPU utilization or custom metrics, to match the load and maintain optimal performance.
Monitoring and Logging:
Prometheus:
A monitoring and alerting toolkit that collects and stores metrics as time-series data, enabling you to monitor the health and performance of your services.
Grafana:
A visualization tool that integrates with Prometheus to create dashboards for visualizing metrics, providing insights into the performance and status of your system.
Loki and Promtail:
Loki: A log aggregation system designed to work seamlessly with Grafana. It collects logs from various sources and stores them efficiently.
Promtail: An agent that collects logs and sends them to Loki for aggregation and visualization in Grafana.
Networking Components
Ingress:
Description: Manages external access to services in a Kubernetes cluster, typically providing HTTP and HTTPS routes to services. It acts as an entry point for incoming traffic, directing it to the appropriate services based on defined rules.
Azure Load Balancer:
Description: Distributes incoming network traffic across multiple backend instances, ensuring high availability and scalability of applications. It can operate at different layers (such as TCP, UDP, or HTTP), providing flexibility in load-balancing configurations.
Cluster Autoscaler:
Description: Automatically adjust the size of a node pool based on the resource requests of your workloads. When pods cannot be scheduled due to insufficient resources, the autoscaler increases the number of nodes. Conversely, when nodes are underutilized, the number of nodes is reduced to optimize cost.
Container Registry (ACR):
Description: Dockerized images of all services will be stored in the Azure container Registry (ACR). This managed service offers a secure and centralized location for managing container images.
● Enhanced Security: Built-in vulnerability scanning.
● Cost-Effective: Optimized for cost with regional storage options.
● Efficient Integration: Works seamlessly with CI/CD pipelines like GitHub Actions.
Storage: Azure Blob Storage:
Azure Blob Storage is a scalable, secure, and cost-effective object storage service designed for storing unstructured data, such as text, images, videos, and backups. It allows users to store large amounts of data in the cloud, with support for different access tiers (hot, cool, and archive) to optimize costs based on data access patterns. Azure Blob Storage is highly durable, offering features like automated replication, encryption, and access control to ensure data protection. It seamlessly integrates with Azure services, making it ideal for applications that require scalable and reliable data storage.
MongoDB Disaster Recovery:
Daily Backups to Cloud Storage:
Install and Configure Mongodump: Ensure Mongodump is installed on the virtual machine instance where MongoDB is running.
Create a Backup Script: We will use shell script to run Mongodump and upload the dump to our bucket.
MongoDB Atlas:
We plan to transition to MongoDB Atlas in the production environment when the user base exceeds 100,000. MongoDB Atlas offers a fully managed database service that ensures high availability, scalability, and robust security. This migration will enable us to handle the increased data volume and provide seamless user experiences. Additionally, it simplifies database management with features like automated backups, monitoring, and dynamic scaling to meet growing demands.
CI/CD ARCHITECTURE
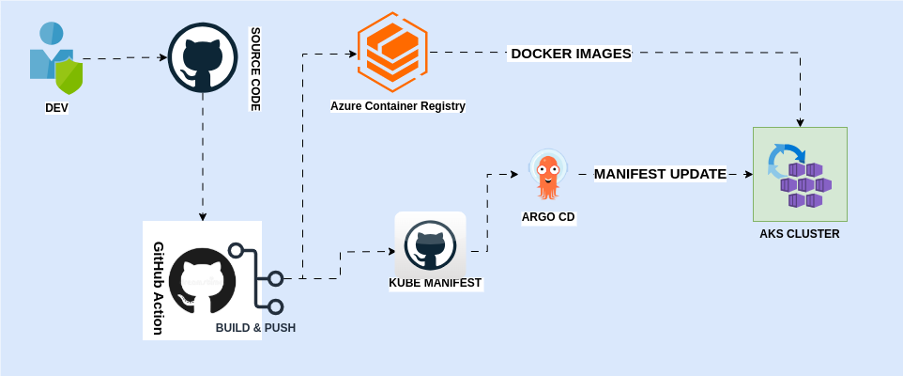
Development Workflow
Source Control
Central Repository: GitHub
● GitHub serves as the primary platform for version control.
● Development teams push code changes, including application code and infrastructure configurations, to GitHub repositories.
Continuous Integration (CI):
Automation Tool: GitHub Actions
● Monitors the repository for any new commits or pull requests.
● Triggers CI workflows automatically upon detecting changes.
Build Process:
● GitHub Actions uses the Dockerfile in the repository to build Docker images.
● Builds are tagged with unique identifiers such as commit hashes or build numbers.
● Tagged Docker images are pushed to the Azure container Registry for centralized storage, version control, and traceability.
● The registry ensures a centralized location for managing Docker images, maintaining version control, and providing traceability.
Continuous Deployment (CD):
Post Successful CI:
● GitHub Actions triggers CD workflows.
● Deployments may include rolling updates depending on the environment.
Manifest Update:
● The CD pipeline updates Kubernetes manifests, which define the desired state of Kubernetes resources such as pods, deployments, and services.
● These manifests are typically stored in a separate GitHub repository dedicated to deployment configurations, separate from the source code repository.
● The CD pipeline updates the Kubernetes manifests with the latest Docker image tag, ensuring the deployment configuration references the newly built Docker image.
ArgoCD Sync:
● ArgoCD, a continuous deployment tool for Kubernetes, monitors the Kubernetes manifests repository for changes.
● ArgoCD synchronizes the Kubernetes deployments with the updated manifests when changes are detected.
● ArgoCD ensures that the desired state of the Kubernetes cluster matches the state defined in the manifests, automatically deploying or updating Kubernetes resources as necessary.
Rollout History:
● ArgoCD maintains a history of deployments, including the version of the application deployed and any changes made to the deployment configuration.
● This rollout history provides visibility into past deployments and allows for easy rollback to previous versions if needed, ensuring reliability and stability in the deployment process.
Summary
This integrated CI/CD pipeline automates the software delivery process, from code changes to deployment, enabling teams to rapidly and consistently deliver updates to Kubernetes clusters with minimal manual intervention.
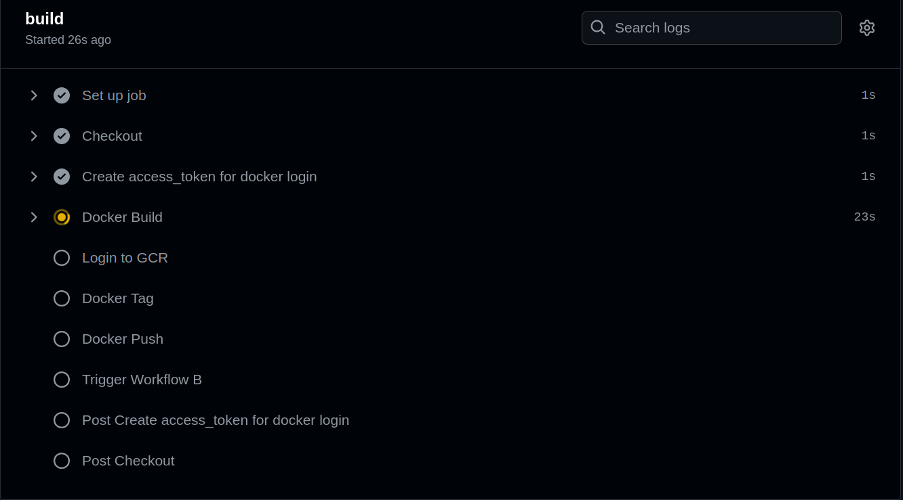
CI STAGE VIEW
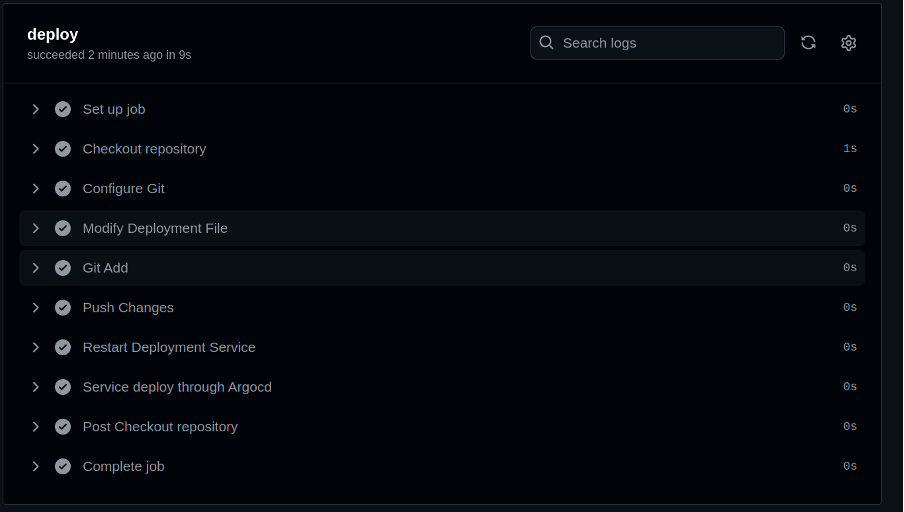
CD STAGE VIEW
Conclusion:
This detailed infrastructure overview highlights the key components of our environment, including Azure Virtual Machines, Azure Kubernetes Service (AKS), backend services, networking components, storage solutions, and database resources. GitHub Actions plays a crucial role in our CI/CD pipeline, enabling seamless automation of build and deployment processes. Together, these components support our development, deployment, and data management processes, ensuring scalability, reliability, and efficiency in our infrastructure.